Everything on the cloud moves fast, from software development to the deployment. But this speed also means there are more places for hackers to attack. Relying on slow, manual security checks slow down everything and makes risks much bigger.
DevSecOps is the essential practice every software development company must follow to deal with this. It’s a complete shift in how teams work and how systems are built, making security a shared, constant job across the entire process, from the moment code is first saved until the app is running live.
From devsecops definition to best practices, we have covered everything about this methodology in our post.
What is DevSecOps?
The meaning of devsecops is adding security steps right into your normal software development process (DevOps). It’s about how people think, the steps they follow, and the use of automation, where security is treated as a shared, primary job for development, operations, and security teams. The main goal is to get security feedback earlier in the development process called “shifting left”. This fixes problems when they are easiest and cheapest to sort out.
How DevSecOps Differs from DevOps and Traditional Security
Old security methods often worked alone, using checklists and acting as a final “blocker” right before deployment. This created a lot of delay and frustration. DevOps brought development and operations together to speed things up, but often missed the security risks created by that speed.
DevSecOps finishes this process. It puts security experts, automated tools, and rules right into the automated build and release pipeline (CI/CD). Security moves from being a reaction/blocker to being a constant, helpful part of the process which makes devsecops different than devops.
What are the Components of a Modern DevSecOps Pipeline
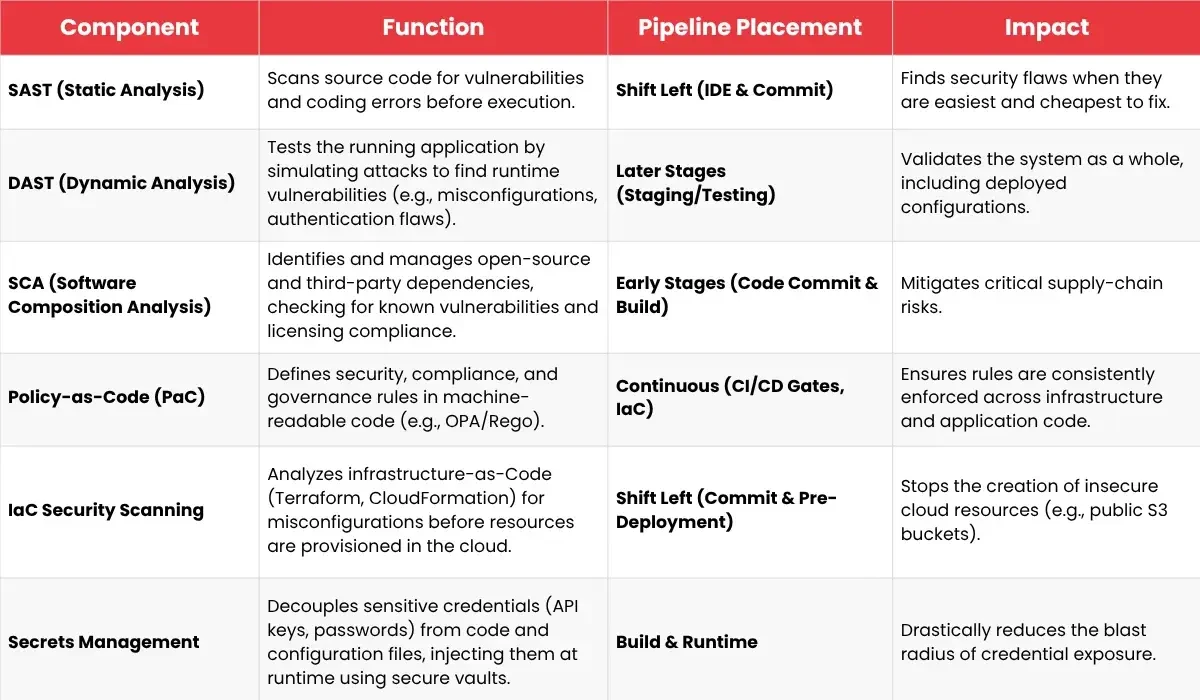
For secure software development using this methodology, the build and release process needs automated tools that give developers quick, useful feedback. Here are the main parts of a modern security workflow:
What are the Benefits of Using DevSecOps for Software Development
DevSecOps isn’t just an expense; it’s a smart investment that pays off by making you faster and safer. Here are a few benefits of using this practice.
Accelerated Velocity and Developer Empowerment
By replacing friction-filled manual checks with automated security controls, DevSecOps directly accelerates the development process. Security feedback is delivered immediately within the developer’s native tools (like the code editor), fostering a culture where every engineer is empowered to take ownership of security. This reduction in context-switching and wait times translates directly into higher output and morale.
- Dramatically lower Lead Time for Changes: You can deploy new features faster, allowing you to react quickly to the market.
- Increased developer productivity: Security advice is helpful and immediate, removing costly delays.
- Fosters shared security ownership: Security becomes a team effort, not just one person’s job.
Also Read: TechOps vs DevOps
Reduced Financial Risk and Automated Compliance
The most significant benefit of the devsecops is cost avoidance. It’s about 100 times more expensive to fix a security bug once the app is running live than to fix it when you first write the code. DevSecOps minimizes financial and reputational damage by drastically reducing the time systems are exposed to known threats. Furthermore, by codifying compliance rules, organizations ensure continuous adherence to complex regulations.
- Lowers Mean Time to Remediation (MTTR): Issues are fixed in hours, minimizing potential downtime and breach impact.
- Reduced Financial Exposure: Avoids the massive costs associated with production breaches and service outages.
- Ensures continuous compliance: Automated Policy-as-Code and reporting (like SBOM generation) provide auditable proof that you are following rules like GDPR and NIST.
How to Implement DevSecOps (Practical Roadmap)

Implementing devsecops is a journey best managed in steps, moving from basic checks to a truly integrated security culture.
- Crawl (Basic Automation): Start with SAST and SCA tools built into the nightly build. Appoint security champions within development teams. Focus on training and fixing the most urgent problems.
- Walk (Integrated Pipelines): Introduce PaC for infrastructure checks. Implement a centralized secrets management solution. Integrate DAST into the testing environment. Use the security problem data to set clear goals for improvement.
- Run (Continuous Security Operating Model): Achieve full shift-left/shift-right capability. Automate SBOM generation. Implement RASP and advanced runtime threat detection. Security becomes a clear, constant, and preventative step that is built into everything you do.
The foundation of this roadmap must be culture: promoting shared responsibility and turning security engineers into helpers who build automated safeguards, not police who block releases.
6 Best Tools and Practices for Implementing DevSecOps in 2026
To win against automated attacks, businesses must do more than just simple scanning. They need to embrace these forward-thinking DevSecOps tools and practices.
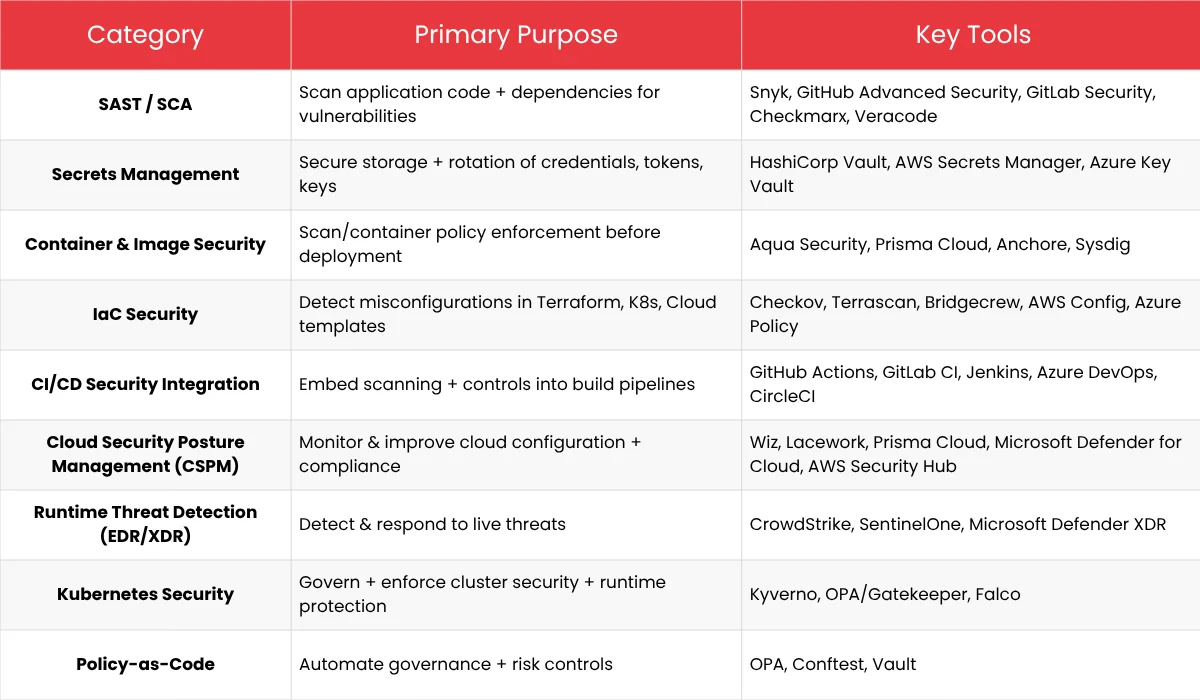
Secure CI/CD Pipelines
Your build pipelines need security too. Use strong logins for access, make sure build servers only exist temporarily, and add a digital signature to all finished software components to prove they haven’t been tampered with before deployment.
SAST/DAST + Dependency Scanning
These are standard testing methods. Dependency scanning (or SCA – Software Composition Analysis) is mandatory; it checks for known security flaws and licensing problems in third-party and open-source packages.
Secrets Management
Passwords, API keys, and connection details hard-coded into the application are a leading cause of security breaches. Secrets management means using secure vaults (like HashiCorp Vault or cloud tools) to keep things like passwords and API keys safe. These tools give the app the keys only when it needs them, ensuring sensitive data is never sitting in the code.
IaC Scanning
Infrastructure-as-Code (IaC) tools (like Terraform, Ansible, or CloudFormation) define the application’s cloud environment. IaC scanning tools check these configuration files for bad settings (e.g., public data storage, weak firewalls) before the cloud setup is created, stopping security holes from appearing in the first place.
Continuous Compliance
Beyond just security, DevSecOps pipelines automatically check software and deployments against company, government, and industry standards, providing real-time compliance dashboards for auditors.
Runtime Threat Detection
This is the shift-right component. Using tools like Runtime Application Self-Protection (RASP) or deep cloud monitoring, teams can notice and sometimes automatically stop threats targeting the live application, such as bad user input or unauthorized file access.
Common Challenges in Implementing DevSecOps
Organizations often face hurdles that slow down their DevSecOps progress. Be ready to overcome these common issues:
- The Culture Silo: The single biggest challenge is failing to get development and security teams to work together. If security is seen as a “police force,” developers will look for ways around the rules. Success requires defining shared security responsibility and making security a celebrated team goal.
- Alert Fatigue (The Noise Problem): If you use too many security tools, developers get flooded with constant alerts, many of which aren’t important. This tires them out, and they start ignoring the tools. The solution is using modern tools with AI-driven prioritization to focus only on the critical, reachable vulnerabilities.
- Tooling Integration Debt: Buying lots of different tools that don’t easily connect with your existing build process (CI/CD) creates a lot of work to maintain. Choose tools that are designed for deep integration and low maintenance.
What DevSecOps Practices Does Softude Implement to Reduce Vulnerabilities?

As a cloud and devops services provider, Softude uses these devsecops practices in a standard way that is designed for fast-moving environments. Specifically, our focus is on three key areas to significantly reduce the risk of attack:
- Mandatory Pre-Commit Hooks: We enforce small tools that run SAST and basic credential checks before a developer can save their code changes. This ensures simple errors are fixed immediately, saving time and preventing build failures later.
- Automated Dependency Fencing: During the app build, we automatically create a verified SBOM and enforce rules that stop the build if any outside component has a vulnerability score above a set level. This proactive supply-chain security prevents flawed code from getting into the main software library.
- Immutable Infrastructure Scaffolding: Softude uses Policy-as-Code combined with strong IaC scanning to make sure all deployed cloud infrastructure is permanent (immutable) and uses the principle of least privilege. If the deployed cloud system changes away from the secure plan, it’s automatically noticed and fixed by automation tools, greatly reducing the chance of security problems caused by bad settings.
What is the Role of AI in DevSecOps
In 2026, AI is going beyond simple checks to greatly improve DevSecOps:
- Modern Detection and Remediation: AI models can now check huge amounts of data (code, activity logs) to find small, unusual behaviors that might signal a brand-new attack (zero-day) or a sophisticated, hidden threat, offering a significant improvement over old methods.
- Predictive Prioritization: Instead of giving security teams a long list of problems, AI looks at the big picture: Is this security hole in a public part of the app? Can an attacker actually reach the code? This gives developers a small, important list of things to fix first, focusing only on the real business risk.
Conclusion
DevSecOps is clearly the future of secure software development. It’s not a one-time project or a bundle of software licenses; it is a way of working, a major change in culture, teamwork, and how you prioritize automation.
While the threats and tools will keep changing, the real factor that will set successful organizations apart in 2026 is the commitment to continuous improvement. By viewing security problems like technical debt and giving every engineer instant, automated feedback, you can build security that actually matches your pace of innovation.
Ready to build security into your delivery pipelines and fully embrace this new way of working?
FAQs
Q.What Does DevSecOps Stand For?
A.DevSecOps stands for Development, Security, and Operations.
Q.What Is The Difference Between Devops And DevSecOps ?
A. DevOps focuses on integrating Development and Operations for faster delivery. DevSecOps is an extension that explicitly embeds Security practices and automation into every single stage of the DevOps pipeline, prioritizing security from the start (often called “shifting left”)
Q.Which DevSecOps Service Is Best For Cloud?
A.There isn’t one perfect DevSecOps tool, but the best ones are those that focus on the cloud, like Snyk or Checkmarx. They are good because they check your code, your cloud settings, and your third-party parts all in one place.
Q. Is DevSecOps Better Than DevOps?
A.Yes, in nearly all cases, DevSecOps is better than traditional DevOps. The reason is that DevSecOps integrates security checks automatically from the very beginning of development (“shifting left”), which makes fixing flaws about 100 times cheaper and faster than waiting to find them just before an application launches.






