The digital transformation mandate has created a core tension within regulated industries: the need for software velocity versus the immovable expectation of security and compliance.
For sectors like financial services, healthcare, energy, and the public sector, this isn’t just a best practice, it’s survival. Regulatory bodies from the FDA and HIPAA in healthcare, to PCI-DSS in retail, to GDPR and the RBI globally, impose stringent rules that often feel like roadblocks to fast, agile development.
Traditional security models, where compliance checks happen right before deployment (the “security gates”), are fundamentally incompatible with DevOps practices. They create bottlenecks, introduce friction, and ultimately force teams to choose between speed and safety.
The real challenge for organizations operating under heavy scrutiny is balancing compliance, risk management, and delivery speed.
DevSecOps is a cultural and technical methodology designed to ensure this security into every phase of the software development lifecycle (SDLC). When implemented correctly in a regulated environment, it transforms compliance from a burdensome annual audit into a continuous, automated process.
This post outlines best practices for DevSecOps adoption, compliance strategies, and implementation tips.
What is DevSecOps
DevSecOps is a software development philosophy that integrates security practices into every phase of the DevOps (Development and Operations) lifecycle. It is an extension of DevOps, which focuses on speed and collaboration, by making security an equally essential, shared, and continuous responsibility.
The core idea is to “Shift Left” moving security testing and compliance checks from the end of the software development lifecycle (SDLC) to the beginning, or the “left” side of the pipeline.
How to Implement DevSecOps?
1) Understand Your Regulatory Landscape Early
The first, and most foundational, step in adopting devsecops in regulated industries is defining your compliance perimeter. You cannot automate a rule you haven’t clearly identified.
Map Relevant Frameworks and Controls
Start by creating a matrix of the relevant regulatory frameworks your organization must adhere to. This might include:
- Financial Services: PCI-DSS, SOC 2, Sarbanes-Oxley (SOX), Basel III.
- Healthcare: HIPAA, HITECH Act, FDA 21 CFR Part 11.
- European Operations: GDPR, NIS Directive.
Once the frameworks are mapped, you must drill down into the specific controls that impact the engineering process. For instance, HIPAA requires encryption of protected health information (PHI) both in transit and at rest. PCI-DSS mandates specific firewall configurations and strict change control.
Compliance as a Design Input
Too often, compliance is treated as a final-stage sign-off. In a DevSecOps model, you must treat compliance requirements as essential design inputs. If a security control (e.g., specific logging or access revocation logic) is required by law, it should be part of the initial architecture review and baked into your Infrastructure as Code (IaC).
Tip Takeaway: Identify control owners, secure clear required documentation up front, and make compliance a non-functional requirement from Day 1.
2) Build a Shared Security Responsibility Model
In a high-velocity environment, the “Security Team says no” mentality is toxic and leads to shadow IT. DevSecOps mandates that security is everyone’s job. To ensure that, have a clear responsibility framework.
A Responsibility Assignment Matrix (RACI) defines who is Responsible (doing the work), Accountable (owning the decision/outcome), Consulted, and Informed for key security tasks. For example:
- Developers: Responsible for fixing code vulnerabilities identified by SAST tools.
- Security Team: Accountable for defining the security standards, selecting the tools, and validating threat models.
- Operations/SRE: Responsible for maintaining golden pipelines and policy-as-code enforcement.
By fostering a culture where security is a measurable part of the developer’s success, you move from gatekeeper to enabler. Implement monthly security ownership reviews where teams discuss and prioritize their security debt alongside their feature backlog.
4) Integrate Threat Modeling in Early Stages
The most effective way to shift left is not just to scan code earlier, but to think about risk earlier. Threat modeling is the structured process of identifying potential threats and vulnerabilities in an application and its architecture.
Why Shift-Left Threat Modeling Matters
In regulated settings, a security flaw is not just a bug; it is a potential regulatory violation leading to massive fines. Threat modeling helps you ask and answer critical questions during the requirements and design phases:
- Where does sensitive data flow?
- What security controls protect the boundary between public and private clouds?
- What happens if an external dependency is compromised?
Common devsecops adoption frameworks like STRIDE (Spoofing, Tampering, Repudiation, Information disclosure, Denial of service, Elevation of privilege) or PASTA (Process for Attack Simulation and Threat Analysis) provide structure for these discussions.
Example: Catching a data-flow risk like transmitting unencrypted Personal Identifiable Information (PII) to a logging service during an architectural diagram review is exponentially cheaper and faster to fix than discovering it post-deployment during a penetration test, which could delay a critical release.
5) Automate Security & Compliance Checks
Automation is the engine of DevSecOps. In regulated industries, it serves a dual purpose: it reduces human error in security, and it provides immutable evidence of compliance.
CI/CD-Native Scanning as Guardrails
Your Continuous Integration/Continuous Delivery (CI/CD) pipeline must become the central enforcement point for all security and compliance policies.
Implement various scanning tools directly within the pipeline stages:
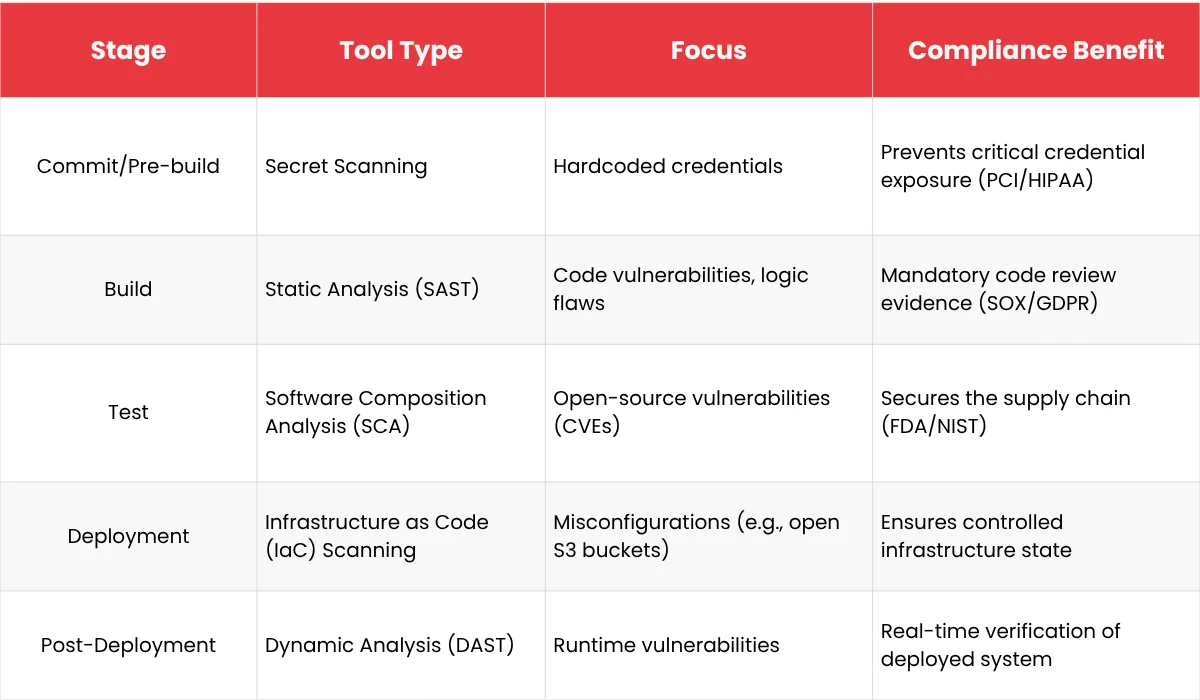
Automation generates the required audit evidence (logs, scan reports, enforcement decisions) automatically. This reduces the need for manual audit checklists and dramatically speeds up the evidence-gathering process when auditors arrive.
Tip: Treat this devsecops automation as guardrails, not gates. If a low-severity vulnerability is found, log it and allow the build to proceed, but enforce a policy that critical and high-severity issues (especially compliance-critical ones) automatically break the build. This reduces slowdowns while maintaining security integrity.
6) Standardize Secure Build & Deployment Pipelines
In regulated environments, consistency is synonymous with control. Every deployment should use the same set of security controls, regardless of the team or application.
Golden Pipelines and Immutable Infrastructure
Golden Pipelines are standardized CI/CD templates (often shared across the organization) that have all the necessary security and compliance steps pre-integrated.
- Standardized Tools: Every service uses the same security tooling, generating uniform output.
- Mandatory Stages: Compliance checks (e.g., data classification verification, logging requirements) cannot be skipped.
- Immutable Infrastructure: Never make changes to running servers or environments. All changes must be made in code, deployed via the golden pipeline, and result in replacing the old environment with the new.
The benefit is consistent controls and highly predictable audit outcomes. When an auditor asks how you ensure all environments meet baseline security, your answer is simple: “They all run through the same standardized, enforced, and continuously audited pipeline.”
7) Leverage Infrastructure as Code for Auditability
Infrastructure as Code (IaC) is crucial for agility, but in regulated settings, its primary benefit is auditability and control traceability.
Version Control and Policy as Code
When you define infrastructure (networks, databases, access rules) using tools like Terraform or CloudFormation, you gain:
- Traceability: Every change to infrastructure is visible, versioned, and tied to a code commit and a deployer. This is essential for meeting change control requirements (e.g., SOX).
- Reduced Config Drift: You eliminate the “snowflake” server problem, where manual changes cause environments to deviate from the secure baseline.
Policy Enforcement with Policy as Code
Implement Policy as Code (PaC) using frameworks like Open Policy Agent (OPA) or vendor-native tools. PaC allows you to write compliance rules (e.g., “All databases must be encrypted at rest,” “No external-facing load balancers without WAF”) and enforce them before the infrastructure is provisioned.
8) Continuous Compliance Monitoring
Compliance can no longer be a once-a-year event where teams scramble to gather evidence. You must move from an annual checkbox to real-time compliance.Here is one of the best compliance strategies for successful devsecops adoption.
Real-Time Monitoring and Reporting
Continuous compliance monitoring involves observing your live production environments to ensure they haven’t drifted out of the secure configuration defined in your pipeline.
A few devsecops tools to use in this phase are:
- Cloud Security Posture Management (CSPM): Scans cloud accounts (AWS, Azure, GCP) to identify misconfigurations against defined industry benchmarks (e.g., CIS Foundations Benchmark).
- Security Information and Event Management (SIEM): Aggregates logs to detect suspicious activity and ensure required logging levels are maintained.
- Governance, Risk, and Compliance (GRC) Platforms: Integrates data from the above systems to provide a single dashboard showing compliance status against multiple regulatory standards in real-time.
This proactive approach generates reporting that auditors actually accept, a continuous feed of evidence that proves controls are operational, not just documented.
9) Secure Supply Chain & Third-Party Dependencies
The greatest risk often lies not in your own code, but in the software components you consume. For regulated entities, securing the software supply chain is paramount.
SBOM and Vendor Risk Management
Software Bill of Materials (SBOM) creation must be a mandatory, automated step in your CI/CD process. An SBOM is a formal, machine-readable inventory of all components in your application (both internal and third-party).
- SCA Tools: Use Software Composition Analysis (SCA) tools to automatically generate the SBOM and cross-reference it against known vulnerability databases (CVEs).
- Secure Artifact Registries: Never pull dependencies directly from the public internet (e.g., npm, Maven Central). Use a secure, internal artifact registry that proxies and scans external dependencies before allowing developers access.
- Vendor Risk Scoring: Maintain a rigorous process for assessing the security posture of any third-party tool or service you integrate with (e.g., payment processors, analytics tools).
10) Culture Shift: Train, Coach, Reinforce

Technology alone cannot solve a security problem; people are the critical factor. DevSecOps requires a profound culture shift where developers and security engineers see themselves as allies.
The Security Champions Program
The most effective way to scale security knowledge is through a Security Champions program. Identify passionate developers, engineers, and ops staff within each team and train them as embedded security experts.
- Role: Security Champions act as the first line of defense, perform initial code reviews, and serve as the liaison between their delivery team and the central Security team.
- Incentivizing: Recognize and incentivize secure design and early reporting of risks. Make security a celebrated contribution, not a punished mistake.
This continuous cross-team learning is how knowledge spreads, and it is how regulated organizations ensure their most valuable asset, their employees, are their best security control.
11) Pilot Small Before Enterprise-Wide Rollout
DevSecOps is a transformative change, and attempting a big-bang rollout across an entire regulated organization is a recipe for failure and compliance disruption.
The Pilot Approach: Measure, Debug, Scale
Start small. Choose a single product, a non-critical system, or a specific feature team to run a controlled DevSecOps pilot.
- Define Scope: Choose a service that interacts with some regulated data (e.g., PII, not PHI), but is low-risk.
- Implement & Measure: Fully implement the golden pipeline, IaC controls, and new cultural processes on this single pilot team.
- Gather Metrics: Use the metrics below to quantify success.
- Debug & Refine: Fix the friction points (e.g., scan times, false positives, training gaps) identified in the pilot.
- Scale: Document the successful process and use it as a playbook for rolling out to other teams.
How to Measure the Success of DevSecOps Adoption
If you can’t measure it, you can’t manage compliance. In a regulated environment, metrics should tie directly to risk reduction and velocity gains.
- Time to Remediate (TTR) Critical Vulnerabilities: The speed at which a critical flaw is moved from identification to production fix. A low TTR proves agile risk management.
- Percentage of Automated Controls: The proportion of mandatory compliance controls (e.g., logging, encryption checks) that are enforced and verified automatically in the CI/CD pipeline. The goal is near 100%.
- Release Velocity Impact: Track deployment frequency and lead time. DevSecOps should increase these numbers by eliminating security bottlenecks, proving it is a business accelerator.
- Compliance Violation Reduction: A direct measure of policy effectiveness—the number of policy violations caught by pre-deployment scanners versus those found in production.
Avoid These Common Pitfalls During DevSecops Implementation

Even with the best intentions, regulated organizations frequently trip over common mistakes during the implementation of DevSecOps:
- Treating DevSecOps as Tooling Only: Buying a dozen scanners and handing them to developers without process changes or training. This leads to alert fatigue and resentment.
- Bolting On Security Late: Implementing DevSecOps by simply putting a giant SAST scan at the end of a traditional CI pipeline. This still creates a compliance gate that delays delivery.
- Over-Engineering Compliance Workflows: Creating overly complex PaC rules or manual sign-off steps that nobody understands or follows. Keep compliance rules simple, testable, and automated.
Conclusion
Adopting DevSecOps in regulated industries is far more than an IT initiative; it is a business survival strategy.
By systematically shifting security left, integrating compliance from the design phase, automating checks through golden pipelines, and fostering a shared culture of ownership, you fundamentally transform your risk profile. You move from being an organization hampered by regulation to one that uses security and compliance as a competitive advantage.
When you treat continuous compliance as a core business process, you don’t just win audits; you deliver faster, safer, and build a foundational level of trust with customers and regulators alike.
Frequently Asked Questions (FAQs)
How Does Softude Handle Threat Modeling?
We start by taking a close look at how your system works, how data moves, where it’s stored, and where things could go wrong. From there, we run safe “attack simulations” to see if any weaknesses can be exploited. You get a clear report with what we found and how to fix it.
Is DevSecOps Hard to Implement?
Devsecops adoption can feel like a big shift at first, but it’s very doable. Most teams succeed by starting small, add a few security checks into the build process, train the team, and grow from there. Over time, security just becomes part of how you work.
How Do You Apply DevSecOps Across The Sdlc?
The main goal is to “Shift Security Left,” meaning you move security checks from the end of the process to the beginning. Here’s a simple breakdown of what Softude does in each stage:
- Plan for risks early
- Write code using good security practices
- Run automated scans when you build
- Test for security issues along with normal testing
- Deploy safely with proper approvals
- Watch for threats in production
- Use what you learn to improve



